The NSA’s recent assessment of the Volt Typhoon campaign offers a sobering lesson that every American business leader must heed. While officials declared the Chinese state-sponsored group “not successful” at maintaining persistent access to critical infrastructure, this apparent victory masks a far more dangerous reality: Chinese cyber threats against US companies have reached unprecedented levels, demanding immediate and decisive action to protect our customers and operations.
Beyond Volt Typhoon: The Expanding Chinese Cyber Campaign
The TechRadar report on Volt Typhoon’s failed persistence in critical infrastructure tells only part of the story. What the NSA didn’t emphasize is that this represents just one campaign among dozens of sophisticated Chinese operations targeting American businesses. The scale of the threat has exploded beyond what most executives realize.
According to the latest intelligence, Chinese cyber espionage activity surged by 150% in 2024, with some sectors experiencing attack increases of up to 300%. This isn’t opportunistic cybercrime—it’s a coordinated, state-sponsored campaign designed to steal intellectual property, disrupt operations, and position for future conflicts.
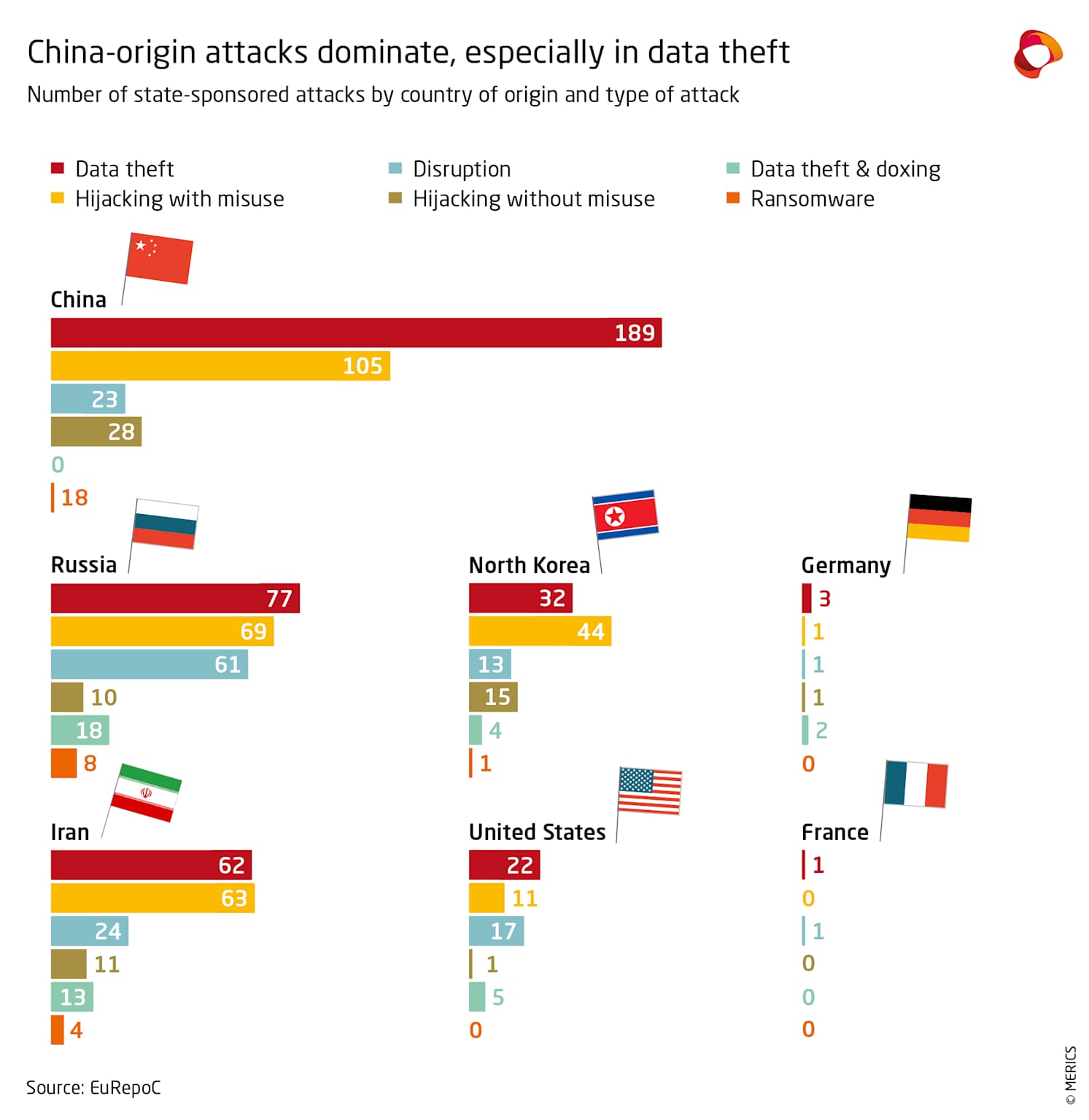
China leads in state-sponsored cyberattacks, especially data theft, posing significant risks to US companies and highlighting the need for enhanced cybersecurity (Metrics report)
The Numbers Don’t Lie: A Crisis in Real Time
The data paints a stark picture of an adversary that has fundamentally changed the cybersecurity landscape. Chinese state-sponsored groups aren’t just probing for weaknesses—they’re executing systematic campaigns across multiple sectors with unprecedented sophistication.

Manufacturing companies now face the highest risk, with Chinese groups targeting 26% of all cyberattacks globally. Financial services and media companies have seen 300% increases in targeted attacks. The telecommunications sector has been particularly hard hit, with Salt Typhoon successfully breaching nine major US carriers, including AT&T, Verizon, and T-Mobile.
The Salt Typhoon Breach: A Case Study in Persistent Threats
While Volt Typhoon may have failed to maintain persistence, Salt Typhoon succeeded where others couldn’t. This Chinese group didn’t just breach telecommunications networks—they maintained access for months, collected millions of phone records, and gained access to court-authorized wiretapping systems.
The implications are staggering. Salt Typhoon could:
-
- Geolocate millions of Americans through their phone data
-
- Record phone calls at will from high-value targets
-
- Access sensitive government communications during a critical election period
-
- Collect metadata from over a million users, including political campaigns
Federal officials have confirmed that Chinese hackers remain active in US telecommunications networks six months after the investigation began, proving that removing sophisticated state-sponsored actors is far more challenging than initial assessments suggested.
The Economic Battlefield: Trillions at Stake
The financial impact extends far beyond individual companies. Chinese cyber operations cost the US economy between $57-109 billion annually, according to White House estimates. But this figure only captures direct costs—the true damage includes:
-
- Intellectual property theft worth trillions of dollars from multinational corporations
-
- Competitive advantages lost to Chinese companies using stolen technology
-
- National security implications from compromised defense contractors
-
- Consumer trust erosion following major data breaches
APT 41, one of the most prolific Chinese groups, has stolen intellectual property from approximately 30 multinational companies across manufacturing, energy, and pharmaceutical sectors. The stolen blueprints include everything from fighter jets and helicopters to cutting-edge drug formulations.
Critical Infrastructure Under Siege
The Chinese strategy extends beyond corporate espionage to critical infrastructure targeting. Recent campaigns have focused on sectors that underpin American society and economic stability.
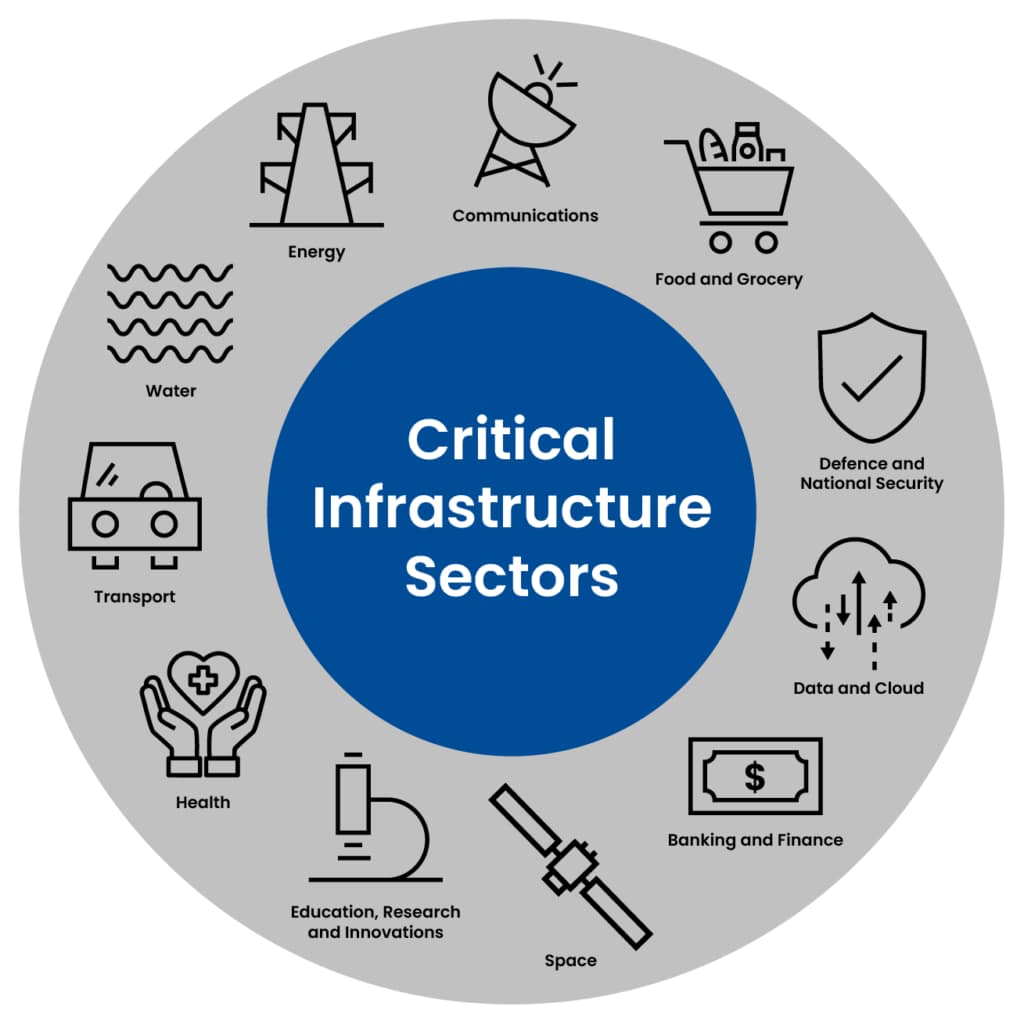
Critical infrastructure sectors vulnerable to cyber attacks include energy, communications, finance, health, and national security
Chinese groups have successfully penetrated:
-
- Energy systems including power grids and utility companies
-
- Transportation networks affecting ports and logistics
-
- Water treatment facilities threatening public health
-
- Healthcare systems compromising patient data and medical research
-
- Financial services targeting trading systems and customer data
The targeting of Guam’s power authority exemplifies this strategy. As the primary power source for a major US military base, compromising the GPA could cripple American defense capabilities in the Pacific.
The New Reality: Seven New Threat Groups in 2024
The threat landscape evolved rapidly in 2024, with cybersecurity researchers identifying seven new Chinese APT groups. Five of these groups demonstrated unique tactics and specialized tradecraft, suggesting a maturing ecosystem of state-sponsored cyber operations.
These groups represent a shift from “smash-and-grab” operations to mission-specific intrusions with clear strategic objectives. They demonstrate:
-
- Advanced persistence techniques that evade traditional security measures
-
- Supply chain targeting to maximize impact across multiple victims
-
- AI-powered social engineering to improve phishing success rates
-
- Cloud-focused attacks exploiting remote work vulnerabilities
The Executive Imperative: Why Leadership Must Act Now
The Chinese cyber threat isn’t a distant concern—it’s a present danger requiring immediate executive attention. The complexity of modern cyber operations demands leadership that understands both the technical and strategic implications.

Board-level engagement is no longer optional. Directors must understand that cybersecurity failures can result in:
-
- Regulatory penalties reaching hundreds of millions of dollars
-
- Shareholder lawsuits for inadequate risk management
-
- Market share losses due to compromised competitive information
-
- Operational disruptions affecting customer service and revenue
The average cost of a cybersecurity incident now exceeds $27 million per event, with some breaches resulting in losses exceeding $100 million when IP theft and competitive damage are included.
Building Asymmetric Defenses: A Strategic Framework
Defending against state-sponsored threats requires thinking beyond traditional cybersecurity approaches. Companies must adopt asymmetric strategies that leverage unique advantages while addressing fundamental vulnerabilities.
Immediate Actions for Executive Teams
1. Implement Zero-Trust Architecture
-
- Assume all network traffic is potentially hostile
-
- Require continuous validation for all access requests
-
- Segment networks to limit lateral movement
-
- Monitor user behavior for anomalous activities
2. Strengthen Identity and Access Management
-
- Deploy phishing-resistant multi-factor authentication
-
- Eliminate SMS-based authentication for privileged accounts
-
- Implement privileged access management (PAM) solutions
-
- Regularly audit and revoke unnecessary access permissions
3. Enhance Supply Chain Security
-
- Assess third-party vendor security postures
-
- Implement secure software development practices
-
- Monitor supply chain communications for anomalies
-
- Establish incident response procedures for vendor breaches
4. Invest in Threat Intelligence
-
- Subscribe to government threat intelligence feeds
-
- Participate in industry information sharing programs
-
- Conduct regular threat landscape assessments
-
- Maintain relationships with law enforcement and federal agencies
Long-Term Strategic Investments
Advanced Persistent Threat Detection
Deploy endpoint detection and response (EDR) and extended detection and response (XDR) solutions that can identify sophisticated threats using behavioral analysis and machine learning.
Cyber Resilience Planning
Develop comprehensive incident response plans that assume successful breaches and focus on rapid containment, data protection, and business continuity.
Employee Training and Awareness
Implement regular security awareness training that specifically addresses nation-state tactics, including spear-phishing, social engineering, and insider threat indicators.
The Path Forward: Turning Threat into Opportunity
The Chinese cyber threat represents both a challenge and an opportunity. Companies that proactively address these risks will gain competitive advantages through:
-
- Enhanced customer trust from robust data protection
-
- Improved operational efficiency through secure digital processes
-
- Regulatory compliance reducing legal and financial risks
-
- Innovation protection safeguarding intellectual property investments
The key is viewing cybersecurity not as a cost center but as a strategic enabler of business growth and competitive advantage.
Your Move: The Time for Action is Now
The NSA’s assessment of Volt Typhoon should serve as a wake-up call, not a reassurance. While one campaign may have failed to achieve persistent access, dozens of others continue to threaten American businesses daily. The question isn’t whether your company will be targeted—it’s whether you’ll be prepared when the attack comes.
The stakes have never been higher. Chinese cyber operations represent an existential threat to American business competitiveness, national security, and economic prosperity. But with the right strategies, investments, and leadership commitment, we can turn this challenge into an opportunity to build more resilient, secure, and trustworthy organizations.
The time for incremental improvements has passed. The time for transformational security leadership is now.
What’s your next move?
We can help. Talk with one of our experts today.

